| Support |
|
We give support to our customers with the aim the ICT would reprent a leverage for the busines and not just a cost center. Thanks to our transversal competences on al the ICT world we are able to guide the strategic choices.
Our capabilities range from in-depth knowledge of systems, especially Unix and Linux, developed in large data center projects and in supporting them. To the definition of complex hardware architectures in high availability or load balancing, clustered or hot stand-by. To the in-depth database knowledge, MySQL, Qracle, MsSQL, SQLite, Oracle Berkeley commercial and open source in the architecture building, and management of complex queries and store procedures.
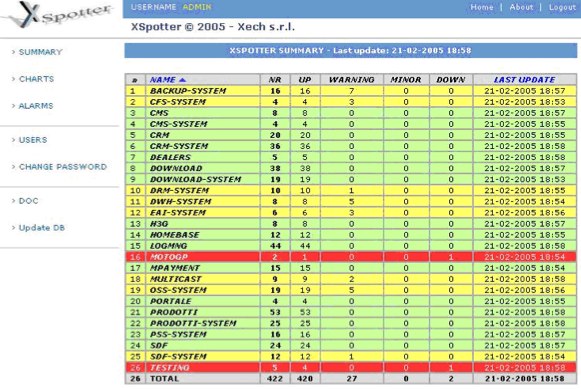
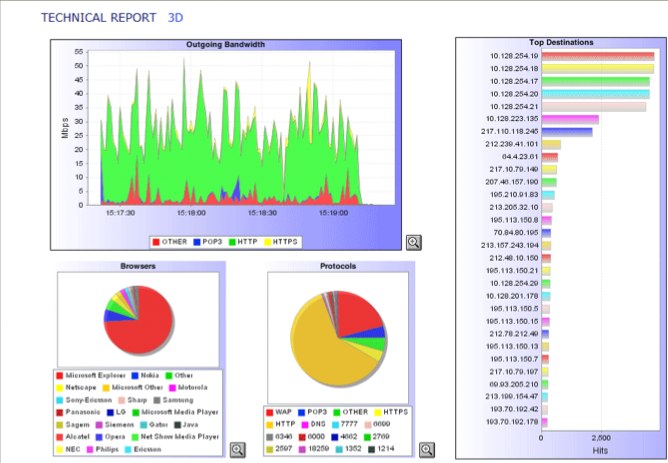
The monitoring of complex systems is a fundamental aspect of Operation. We have developed over the years a very important experience in this field so as to define a new concept of monitoring, service-oriented more than system-oriented. Normally the most popular monitoring platforms are limited to measuring the basic parameters of the key systems inside the service, so you have alarms in the event of a critical nature of these parameters (disk full, web server down, network connection down, db overload ) but no one of them does an audit of the service. A service is intended as a set of homogeneous elements that must work in synchrony and with certain connections between them. So it happens that the individual components are all ok in terms of "life" parameters but the service is not "alive" (think the classic error page on the web server: it's active, but a timeout, a cluster switch or a data loss in the db produce an error). Our monitoring system combines complex controls (for example, simulating the client navigation) in a group so you have control of the service. Read more ...
Network security is a very critical IT domain. It's often overlooked or held in due consideration because there is no direct link between the invested capital and revenues of this investment. So happens that small businesses are not well equipped because they decide to invest in other directions related to the business and large companies invest an important quote on the security solutions from the large providers but in both cases there isn't a process of information security. Basically the security is a complex domain that first of all starts with a risk analysis based on the assets and company business, a step that is often overlooked or just not considered. Then we come to the definition of critical areas, giving weight to the various risks identified. You define a budget for the security that is proportional to the risk-weighted so not to invest too much or too little and finally have a link between investment and revenues seen as losses avoided. Only at this point we get to the instruments. But the choice should not be left to the suppliers, the largest security companies whose the aim is to sell hardware or solutions. Specialist advice must always include the definition of a business process, the basic training of employees, definition and implementation of procedures, purchasing and installation of the tools in the critical points and finally tuning of alarms and procedures for responding to them. a periodic audit process that ensures the operation. At the end often are not required large investments in technology, but good practice. We have expertise in all these aspects and we guarantee a transversal approach to the problem of information security.
Networking, the IT skeleton, the tubes of the information. It 's very important that the network project is cared with a lot of details to take account of current and future needs. We have experience in the development of data centers with network equipment of major manufacturers (Cisco, Juniper, Huawey) and we can provide support both in the planning phase and implementation, in the operational phase and optimization. |